Modern battlespace is getting more and more transparent especially for mobile warfare. Is it anymore possible to survive in hide and seek game against modern all-weather capable sensors cueing and directing enemy firepower?
M.Sc., Lic.Tech, Dr.Tech h.c., GSO, Colonel Jyri Kosola, R&T Director, Finnish Defence Forces
Disclaimer: The arguments and opinions are solely of the authors and do not necessarily reflect the official position of the Finnish Defence Forces. Feel free to use the text and images, as long as you refer to the source.
Finland might have an answer for this challenge; low cost decoy technology that is easy and rapid to use, allowing credible multi-spectral decoys to be deployed en masse. By investing only 1 to 3 percent of the acquisition budget to credible decoy you can stay alive in the modern battlefield to fight another day.
Developing sensor technologies, especially all-weather capable Synthetic Aperture Radars (SAR) and drone-mounted day & night capable infrared cameras and laser radars (LIDAR) will make the battlespace considerably more transparent than only few year ago. Miniaturization of SARs, LIDARs, hyperspectral cameras and infrared imagers transform the sensor threat from stand-off surveillance and targeting to close-in unmanned systems. Buildings, vegetation, terrain and camouflage will provide less protection against these recce, targeting and attack capable systems. Even stealth will be less effective, as sensors can detect not only targets, but also tracks and trails left by them. There is no treasure at the end of the rainbow, but there will be a target at the end of the vane.
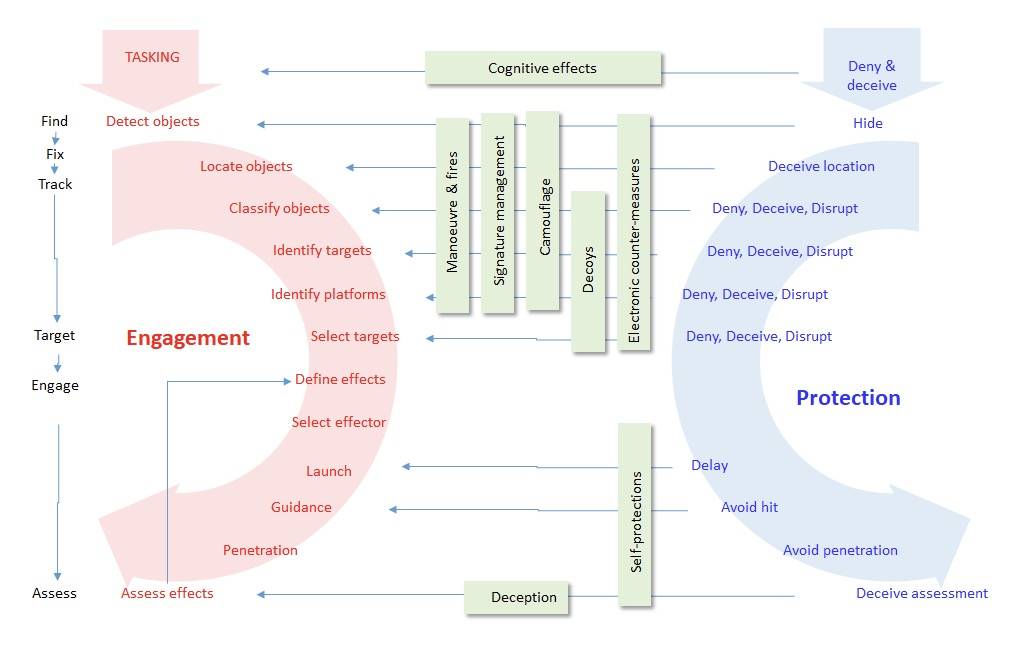
Defender needs to succeed once in breaking the kill chain, but the attacker needs to break every link in the live chain.
Modern targeting processes can connect any sensor to any shooter and commence engagement within few minutes. So, how is it possible to survive in the transparent battlespace?
Survivability requires systemic approach; how to delay, disrupt and deceive hostile processes while securing friendly processes and mechanisms. Attacking hostile process is also called kill chain which the defender tries to break. Defender tries to counter the attacker with his live chain.
From process point of view, the situation is highly asymmetric: if the defender succeeds in breaking the kill chain at any point, the attack fails. On the other hand, the attacker needs to smash every link in the defender’s live chain. From tactical point of view, the asymmetry favors the attacker, who holds the initiative and can choose the time and means for engagement. Both sides need to exploit several different tools in their toolbox.
The defender uses firepower to prevent the enemy from closing in and forcing it to fire at distance where it can’t see the target as clearly as at shorter ranges. Signature management methods and camouflage are used to blend targets in the background. Electronic jamming can help in this by dazzling sensors and creating false targets
Defender will also relocate assets frequently in order to outpace enemy targeting process.
Relocation of the assets is effective only if it takes long enough for the enemy to find out what detected objects to engage. The attacker needs to classify detected objects as militarily relevant or irrelevant (e.g. tank or stone), as critical, important or nonimportant (e.g. command vehicle, missile launcher or utility vehicle) and as friendly, hostile or neutral.
With credible decoys scattered around the battlespace, the defender can create false detections in the enemy targeting process. This will slow it down, as the enemy has to decide which detections are genuine and which false targets.
If the defender has been vice enough to make signatures of different platforms similar, it will be difficult for the attacker to concentrate his firepower on the important targets. Thus, the attacker needs either to wait in order to gather more information, or to divide his resources to all detected targets.

Decoys need to be credible at all wavelengths, but only down to distances depending on the threat. (Image: Kosola)
If there are enough decoys to create detections in the enemy targeting process, the defender can protect himself by overwhelming attacker’s resources. The key challenge is how to acquire and deploy decoys that are in the same time credible, affordable and deployable.
Finnish company Doppelgängerhas developed a novel solution that provides credibility through multispectral signature, affordability through mass production means and deployability through “Ikea logistics”.

Decoys can be deployed by folding them like cardboard boxes. (Image: Kosola)
Multispectral imitation is based on multi-layer structure, where infrared signature is created by thermal elements that are printed on flexible substrate. Also radar decoys can utilize printed electronics. IR and radar decoy elements can be attached on either surface of the material, which itself provides the visual wavelengths replica of the real system. With proper surface material this will fool even hyperspectral imaging systems.
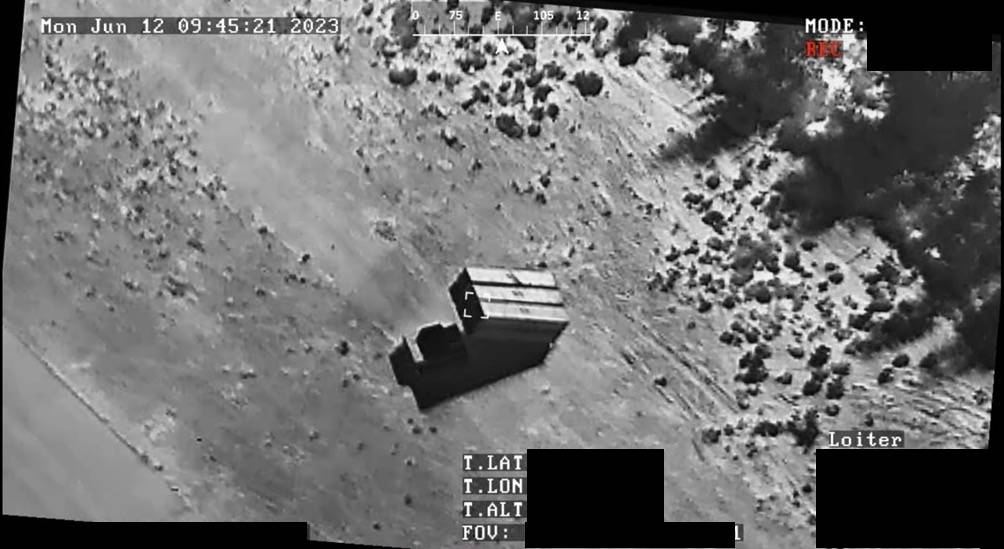
Use of mass-produced structural material and simple printed electronics keep the materiel and manufacturing costs down A simple decoy could cost only few thousand euros. Even complex systems, like missile vehicles, would cost only a tiny fraction of the cost of the system they are protecting by drawing enemy fire from them.

Mass-produced materials, like printed electronics can be used to saturate enemy ISTAR systems. (Image: Kosola)
Using packaging as part of the decoy, and simple folding type construction like in the cardboard boxes, means that two persons can fold open and deploy or repack a decoy in five to ten minutes. This short time means that these decoys, unlike most of the current ones, can be utilized also in offensive operations and mobile warfare.
Credible multi-spectral decoys, deployed en masse, can help us to hide in the open, transparent battlespace. By investing only 1-3% of the acquisition budget to decoys, one can remarkably increase the lifetime expectations of the real system in the modern battlespace.

